What Is Zero Trust?

Life was much simpler 20 years ago, network security included. As technology has evolved, so has the complexity of protecting your data. Back then, you could pretty much rely on a perimeter-based “trust but verify” approach. Anyone who could verify their identity within the network could access all resources within the organization. And because most business activities happened within an office on company devices, it was a pretty solid approach.
With great growth comes challenges. In the network, those include security breaches smart enough to surpass perimeter-based security. And with the adoption of cloud computing and the resulting growth of remote work, challenges increased. Trust but verification wasn’t enough. Along came “de-perimeterization”—now known as Zero Trust—to solve for these new security challenges.
The Basics of Zero Trust Today
Based on the concept of “never trust, always verify,” Zero Trust is a foundation of a cyber-resistant organization. The identity of all users must be verified before being granted the necessary privileges to access their organization’s key components, such as applications and data. Success requires not only strategic planning but also employee alignment and participation.
Business complexity continues to grow with hybrid and remote workforce demands, data storage intricacy, and multiple platforms and environments to protect. Also known as Zero Trust Architecture (ZTA), implementation requires a mindset shift. To understand this better, let’s cover a few key terms surrounding ZT.
Key terms to know:
- Continuous verification: This is the backbone of “never trust, always verify.” It requires verification of credentials on any device at any time for any resource. The trickiest part of continuous verification is user experience. You can manage continuous verification through risk-based conditional access. This interrupts a user for verification only when risk levels change, ensuring a smoother employee experience.
- Least privileged access: Provides just the minimal set of permissions to access the system from a productivity perspective, while ensuring the protected data stays secure.
- Identity management: This security control digitally validates device and user identity with security protocols, and one/more factors of authentication.
Zero trust is a cybersecurity strategy premised on the idea that no user or asset is to be implicitly trusted. It assumes that a breach has already occurred or will occur, and therefore, a user should not be granted access to sensitive information by a single verification done at the enterprise perimeter. Instead, each user, device, application, and transaction must be continually verified.
What Zero Trust Is Not
There are a few misconceptions about Zero Trust.
- It’s not a singular product or set of products.
- It’s not a set-it-and-forget-it operation with a one-size-fits-all metric.
- Security is not the only benefit.
- It doesn’t imply a mistrust in your employees.
Zero Trust requires a mindset change, but it’s one that benefits your organization’s security posture and compliance outlook, while reducing complexity and cost over time. It must be continually evaluated, adjusted, and improved according to your unique business needs.
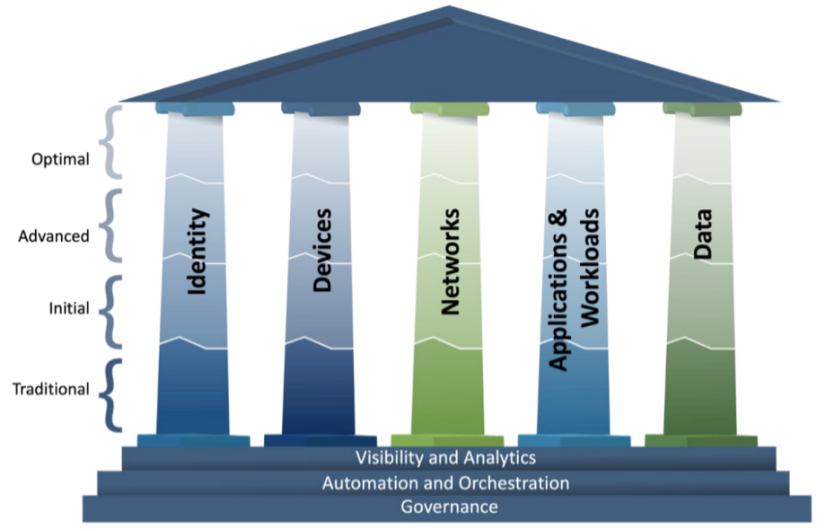
Pillars of Zero Trust
With growing cybersecurity challenges from increasingly remote workforces, an executive order to improve national cybersecurity was issued in 2021. One outcome of this order was the release of the first Zero Trust Maturity Model, or ZTMM, from the National Cybersecurity and Infrastructure Security Agency (CISA). Released in 2023, the latest update expands on the five core pillars of Zero Trust. These pillars outline the growth journey your organization can take in the path to implementing Zero Trust.
The evolution of Zero Trust can look like this:
- You can begin with basically nothing—a traditional, solution—periodic review of permanent access, and create a plan to implement Zero Trust fundaments one pillar at a time.
- Then begin initial automation planning and implementation with basic cross-pillar coordination and some least privileged access planning.
- Advance the automated controls coordinating across the lifecycle of each pillar with least privileged access developing to include risk and position assessments.
- Finally, optimize a fully automated plan with dynamic least privilege access and smooth coordination across all five pillars.
As outlined in the latest ZTMM release, “these maturity stages and the details associated with each pillar allow agencies to assess, plan, and maintain the investments needed to progress toward a ZTA.”
What’s Next?
The Zero Trust Maturity Model will continue to mature (pun intended). While there isn’t one product or set of products that answer all your Zero Trust needs, technology partners like Veritas can make all the difference to smooth Zero Trust planning and positioning.
Learn more about Cyber Resiliency Solutions from Veritas.
