Multifactor Authentication Made Easy with Flex Appliances

Protecting confidential data has always been a priority, whether it’s your personal banking data or an organization’s trade secrets. The need to protect data hasn’t changed. The methods to do it — and the increasing complexity of threats to your data — are constantly evolving.
Preventing unauthorized access to resources, whether networks, personal computers, applications, or accounts, previously centered around passwords. As compute power increased, it became easier to crack user passwords. Requiring people to set more complex passwords and change them more often isn’t enough. To alleviate the problem, organizations are implementing additional methods to better secure user accounts. Of these, multifactor authentication (MFA) is one of the most ubiquitous today.
Basics of Multifactor Authentication
You’ve likely already encountered multifactor authentication in different areas of your digital life. Many service providers require a second level of authentication to log in to a system or an account. Having the login credentials — username and password — for an account doesn’t validate that you are who you claim to be.
Multifactor authentication makes system access more secure by using two or more factors to validate a user. The first factor is something you know (a password), and the second is something you have (an access code or similar). Two-factor authentication (2FA) is the most common example. In 2FA, the second factor is a one-time password or time-based one-time password delivered via a method such as an authenticator application or a text message, email, or phone call to a registered or known account.
Multifactor Authentication on Flex Appliances
The MFA implementation on Veritas NetBackup Flex Appliances is based on open standards and does not require additional hardware or internet connectivity.
Password: Multifactor authentication on Flex Appliances uses a time-based one-time password (TOTP) generated by an authenticator as the second factor. The TOTP is a six-digit code valid for a limited period, such as five minutes. If the time expires before the user completes the login, a new passcode must be generated. The forced expiration makes this method more secure than a one-time password.
Configuration: The initial multifactor configuration prompts an authorized user to generate a random key to create a security token by scanning a QR code from the appliance or entering a custom key from another source. Using the security token, the authenticator instantly generates the passcode to complete the configuration. Once MFA is configured, all future logins require a TOTP and the standard account password.
Enablement: Without enforcement, multifactor authentication configuration is not mandatory, however. Individual appliance users can enable and disable MFA on their respective accounts.
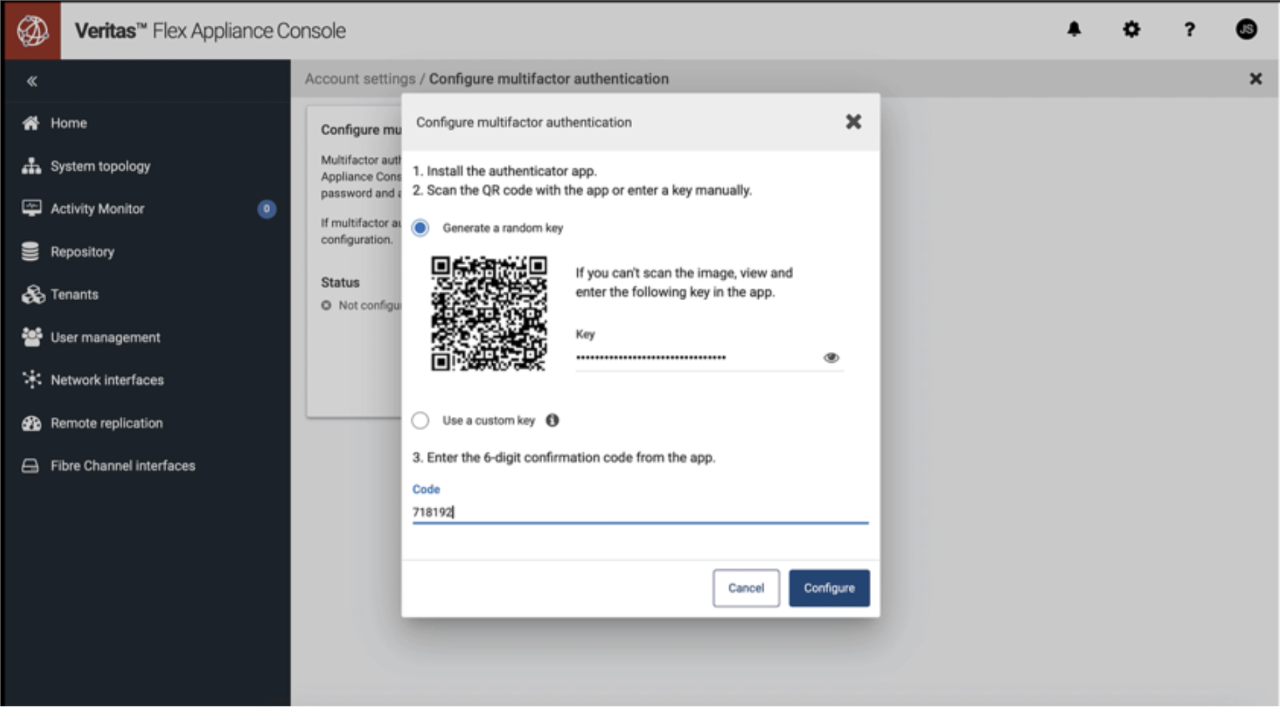

Enforcement: Administrators have the discretion to enforce multifactor authentication. When the enforcement is turned on, all users must configure the second authentication factor within an allocated grace period of no more than 90 days. Once activated, MFA enforcement cannot be disabled.
Management: When managing multiple appliances, you can use the custom key from another appliance to configure the security token. This option eases the administrative burden by eliminating the need for numerous access tokens associated with individual appliances.
In some situations, a user may be unable to generate the six-digit passcode due to an issue such as a lost mobile device, deleted authenticator application, or missing security token. In these situations, a user with a super administrator or security administrator role can reset that user’s multifactor authentication.
Multifactor Authentication Everywhere
Multifactor authentication is available for the following Flex Appliance–hosted services:
Flex Appliance Web UI
Flex Appliance shell
NetBackup WORM (Write Once Read Many) storage server shell
NetBackup 10.3 Primary and Media Server Web UI
NetBackup 10.3 Primary and Media Server shell
Multifactor authentication is only one of many essential security layers implemented on Flex Appliances. It’s an integral part of the Flex architecture and doesn’t require separate licensing.
With Veritas, you’re better equipped to face cybercriminals and ongoing security threats.
Next Steps
- Simply update your data protection infrastructure by downloading Flex 4.0.
- Learn more about Flex Appliance security in our security white paper.
- Explore how the Veritas family of backup appliances can help you meet data protection challenges.
- Discover how easy it is to configure multifactor authentication with our short demo below.
