CrowdStrike and Veritas Deliver Cyber Security and Resiliency

It takes a holistic approach and an expanded ecosystem of cybersecurity partners to be resilient against cyber criminals today. Essentially, it’s an all-hands-on-deck challenge that no single solution or product can tackle. The threats are evolving too fast for a single approach. That is why partnerships are so vital. Working together and collectively sharing knowledge bolsters cybersecurity and helps mitigate the threats.
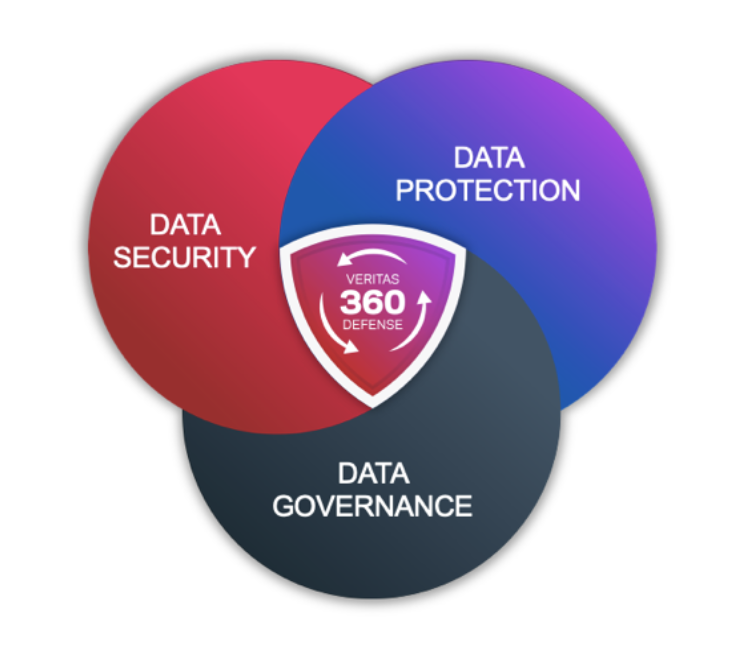
Three months ago, I pioneered a new strategic role at Veritas Technologies. My role focuses on developing cybersecurity technical alliances as part of our Veritas 360 Defense architecture. I am passionate and dedicated to integrating with the champions of the security world.
While studying the cybersecurity landscape, I identified CrowdStrike as one of few security companies that has the depth and breadth of solutions necessary to realize our vision of Veritas 360 Defense.
Connecting with CrowdStrike
I reached out to CrowdStrike with an ambitious slate of proposed cybersecurity solutions that included just about every product at Veritas and CrowdStrike. Executives at Veritas and CrowdStrike indulged my enthusiasm and made introductions to a broader set of colleagues at CrowdStrike.
While I was eager to get started, there was a one hitch: Everyone at CrowdStrike was preparing for their annual Fal.Con conference in Las Vegas. To my surprise, that didn’t stop the momentum! The CrowdStrike alliances team at invited me to Fal.Con in anticipation of a rare face-to-face opportunity to meet with experts from around the world. I jumped at the opportunity.
I packed my bags and dashed off to Vegas with several solutions sketched out and ready to go. We reviewed multiple options and decided to focus our first efforts on a use case that we could test in a real-world environment and make accessible to customers immediately.
So, what was the solution? We decided to test the problem of posture management when restoring applications after an incident.
If you know CrowdStrike, you know that it uses a single, universal agent that observes infrastructure all the time. This universal agent has many capabilities including detection of anomalous behavior, managing data egress through endpoints, and a variety of posture management capabilities. It’s a sophisticated solution.
I want to highlight what happened next. At this busy time, Veritas and CrowdStrike met as a team. We brought together solution architects and IT professionals to test, validate, and document a process that assures infrastructure of optimal threat posture when restored from backup. We detailed the use of CrowdStrike Cloud Security Posture Management (CSPM) with Veritas NetBackup.
Why Does This Matter?
I believe this is an important solution. When a security incident occurs, it’s vital to recover business services quickly. In the worst case, that may include recovering systems from backups. But in the time since a backup occurred, there may be patches available to remediate the attack surface. CrowdStrike CSPM makes it fast and easy to minimize the attack surface.
Of course, CSPM and NetBackup should “just work,” right? And they do, but we also discovered several best practices that ensure best outcomes. We also identified not only what we believe is the optimal process, but documented configurations that save time during the recovery process.
Better still, we validated all of these elements using Veritas infrastructure with Veritas IT professionals.
The Veritas 360 Defense
In some respects, this isn’t “gee whiz” technology—but it is valuable. Our teams successfully validated and documented a process by which you can assure your infrastructure has optimal threat posture when restored from backup. Together, we deliver Veritas 360 Defense. We remove the risk of integration for IT professionals.
It's a great solution and we’re looking forward to building many more solutions together. But that’s not the main takeaway. I want to end my story by telling you how great it is working with CrowdStrike. Their teams were busy when I requested to work with them. Regardless of packed schedules and travel itineraries, everyone leaned into the job of creating solutions. I was impressed with their collaborative energy and giving spirit. They cast a critical eye on every solution I proposed, always guiding the conversation to solutions that we could use. It’s a pleasure working with folks who share goals and values for the collective good.
Learn more about how Veritas 360 Defense provides a blueprint to fight today’s cyber threats.
