5 Key Steps to Holistic Data Security Posture Management

Data security forms the basis of trust and efficiency across every organization. As we begin 2024, your primary priority should be to gain an understanding of your data. Once you understand it, start to classify it. Start adding protection mechanisms to keep it safe.
The day will come (if it hasn’t yet) when you’ll have to recover data from a mishap or cyberattack. A cybersecurity incident response team investigates a new cyber breach every few seconds. A breach can be devastating, exposing sensitive data, causing customer loss, and creating legal ramifications. More than 26% of organizations worldwide experienced a ransomware attack within the past two years according to our recent 2023 Global Report on Data Risk Management.
You need to take five steps to control your data during cyberattacks. These actions will guide your team to a holistic approach to data security posture management. So, what exactly does that mean? A holistic approach to data security posture management is adopting a platform that gives you control to track, protect, and classify your data. It reduces the risk of unauthorized data access and automates the prevention of data theft, exploitation, or exposure.
Step One: Understand Your Data
First, identify the types of data your organization owns. It’s critical to understand and categorize the data in your storage coffers. Both structured and unstructured data are vital to ensuring suitable security measures to protect that data. This also helps address dark data, data for which its value is unknown or redundant, obsolete, or trivial (ROT).
- Structured data is stored in relational databases in tables and rows for efficiency.
- Unstructured data includes email messages, social media posts, and multimedia files.
Data has immense value that is integral to strategic decision-making and operational integrity. But it poses serious risks if mismanaged or unclassified. Any effective solution must provide both efficiency and security. You need a solution to identify the varying data sensitivity levels.
Holistic data security posture management also helps you identify whether sensitive data has been compromised. Your platform will notify all relevant stakeholders, shedding light on access issues. Arming you to identify insider risks and the severity of a cyber incident. Your organization can navigate the intricacies of data management. You gain a better understanding of all assets under management for data protection.
Step Two: Control and Classify Your Data
Next, carefully navigate through your data to gather critical details to categorize your primary and backup data. Data classification is an integral component of safeguarding your organization's data assets. It equips your teams with the information they need when a cyberbreach occurs.
Imagine the unstructured data flowing through your organization daily. It includes everything from documents and images found in emails to audio files from Zoom calls. Without careful oversight, it’s difficult to track the access of that data. Classification is crucial to give your teams visibility to stay ahead of cybercriminals.
Implementing these procedures increases your security posture to comply with industry regulations. It moved you to a more proactive data-management strategy. Safeguarding critical assets by categorizing and monitoring them allows you to store, control, and classify data correctly. All these efforts give you a better vantage point to answer difficult questions during an incident.
Step Three: Monitor Full Access History
Use a zero-trust approach to monitor your entire user-access history using a system that integrates securely with your existing infrastructure. It’s essential to have precise detection and response capabilities to unauthorized access. When you have control of all your data, you can better respond when the storms hit.
Giving your teams unparalleled visibility into all data interactions helps pinpoint problems faster. It's about scrutinizing and gaining actionable intelligence for every data touchpoint. Implementing holistic data security posture management allows you to better govern your data.
Step Four: Back Up and Secure Your Data
Consider backups as a vital lifeboat in a sea of digital data. Back up your data often and secure it autonomously. Ensure it’s impervious to change (immutable) and protected from unauthorized access. Creating multiple backup copies provides more opportunities to recover. Data immutability ensures against unsanctioned encryption and locks your backups. An indelible backup ensures your data survives untampered throughout its existence.
An isolated recovery environment (IRE) goes much further, acting as a fortress around your data in case of a ransomware attack. An IRE keeps backups separate and undiscoverable by anyone on the network. This isolation acts as a shield, protecting both backups and primary data sources from harm. Implementing an IRE creates an environment of vigilant preparedness. Your data — your digital treasure — is safe from whatever comes its way and always ready for action.
Step Five: Be Ready to Recover Your Data
Developing an effective cyber-recovery plan is no longer optional — it’s necessary. A vital element of any data protection plan should include regular tabletop exercises. These simulated cyberattacks let your team practice responding to breach scenarios. They’re like fire drills for your data. By practicing, everyone knows what to do in an actual crisis.
The ideal scenario involves recovering using an isolated, air-gapped approach. This ensures data recovery process occurs outside your primary network, protecting against malware that could interfere with recovery.
We take this step further with Veritas REDLab, our in-house cybersecurity malware testing facility. We validate the cyber-resilience capabilities of our software against different ransomware strains. We battle-test each piece to confirm it can withstand malware attack vectors.
Do not wait for cyberattacks or breaches to remind you of the value of your data. Data breaches don't only cost money; their ramifications reach to affect your brand, customer trust, and market position. Act now, fortify your data, and safeguard your organization’s future. You have an opportunity: Support change within your organization by being a leading advocate for data security, protection, and governance.
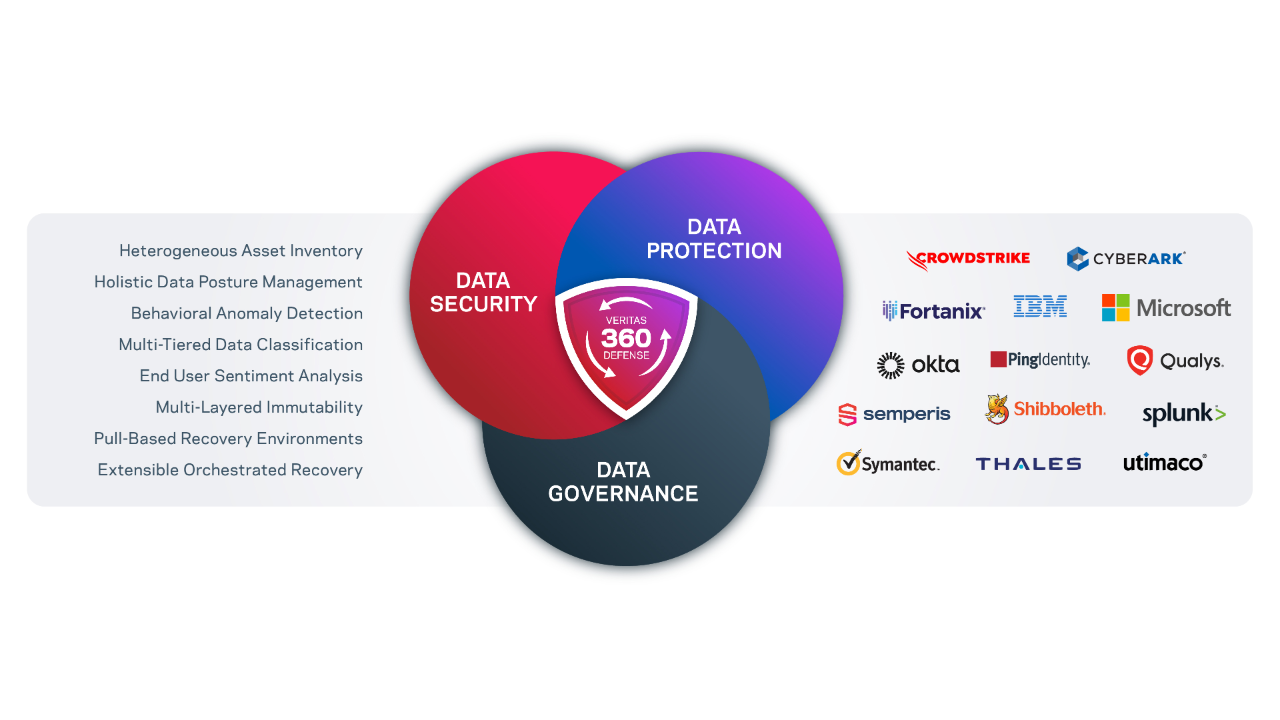
Learn how Veritas 360 Defense provides an asset inventory an an overall approach to fight cyberthreats.
