The Human Factor of Cyber Resilience: The call is coming from inside the house

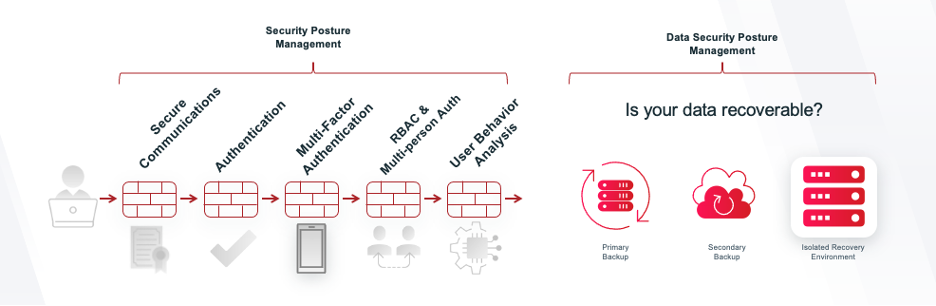
In today's increasingly interconnected digital landscape, the call may indeed be coming from inside the house. Internal threats, such as credential compromise, privileged account abuse, and malicious insiders, pose significant risks to cyber resilience. The key to mitigating these risks lies in identifying and monitoring high-risk end-user behavior without adopting a "big brother" approach. The complexity of managing user behavior across a vast data estate, including various workloads and applications, demands sophisticated solutions. Veritas' User Behavior Analytics (UBA) within Alta Data Protection and NetBackup 10.4 offers proactive self-defense capabilities. These tools enable organizations to detect, mitigate, and respond to threats, ensuring that critical backups remain secure and recoverable.
In Phase Two of the Veritas Cyber Recovery Checklist, organizations are urged to "Identify and monitor high-risk end-user behavior." This doesn't mean you need to adopt an intrusive "big brother" approach, scrutinizing every move your team makes. Let's be honest, you have more pressing priorities than tracking every click. However, you still need to be aware if something suspicious is happening so you can take action and safeguard your data proactively.
According to Securonix 2024 Insider Threat Report, “the number of organizations reporting insider attacks increased…to 76%.” Credential compromise, privileged account abuse, and malicious insiders represent a significant threat to cyber resilience, so it is important to monitor for changes in user behavior. This might sound simple, but when you look across your entire data estate, you will have users with varying levels of credentials across dozens, if not hundreds, of enterprise workloads, databases, PaaS or SaaS applications. Analyzing a single user's activity across the enterprise is complex. Identifying their normal behavior and spotting any irregularities becomes daunting, especially when you need to scale this process for all users across the entire organization.
User Behavior Analytics (UBA) in Veritas Alta Data Protection and NetBackup 10.4 enables proactive self-defense capabilities, and gives the organization critical time to detect, mitigate and respond to threats with layered defenses to slow down the potential attacker from compromising their critical backups.
Adaptive Self-Defense
UBA is a part of our Adaptive Self-Defense technology that focuses on collecting and analyzing user activity data, and establishing a baseline of normal behavior for each user. Data protection systems—or more plainly: backups—serve as the last line of defense for protecting customer and enterprise data against a cyberattack. Veritas proactively defends against user actions that may result in premature expiration of backups, assets being unrecoverable, or lowers the security posture of your system. As you build on your Security Posture Management, it means a bad actor needs to work even harder to hide their tracks in order to access your protected and recoverable data.
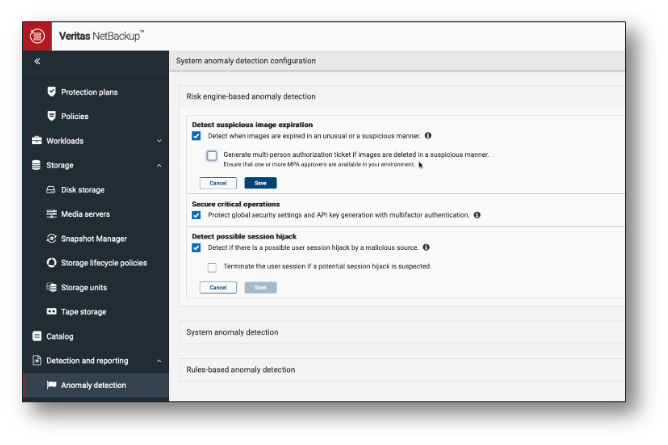
Slowing down an attacker is crucial to give the enterprise time to detect the attack, mitigate damage, and contain the attacker. Detecting host-specific attributes such as an IP address, rate of incoming requests or validating host identity helps quickly surface if an attacker has stolen security tokens from one system and are trying to utilize them on another system to evade detection. NetBackup can automatically log off all sessions of the suspicious user. As announced earlier this year, Veritas User Behavior Analytics uses rich, tamper-resistant audit logging and AI/ML-capabilities to detect anomalies in admin behaviors such as image expiration, any changes in global security settings, and session hijacking.
By continuously analyzing and monitoring for abnormal high-risk operations, triggering alerts, and implementing additional automatic security checks, you can limit risks to your valuable backup system. This approach provides a robust foundation for visibility and aids forensic investigations by tracking changes in the security posture over time. To prevent risk posture elevation in a backup system, we automatically invoke one or more security controls such as in-line MFA prompt (Multi-factor Authentication) or enforce MPA (Multi-person Authorization) request to contain the destructive action. MPA blocks data expiration when it suspects the malicious user is trying to perform an abnormal delete operation or trying to change critical settings that change the security posture of the platform. The change is blocked unless approved by another designated approver. The solution also provides flexibility for the second approver to be obtained from another authentication source—like a SAML 2.0 Identity Provider or using digital Smart Cards—for situations where an attacker may have compromised the Active Directory/LDAP infrastructure.
Self-Learning
These self-defense solutions will slow down a cyberattack and prevent irreversible data destruction operations. User Behavior Analytics leverages machine learning to track historical action, and even self-learns based on MPA approver responses. If an alert is triggered by a legitimate login, the system self-learns so instead of denying access, it will remember the selection and not trigger an alert next time.
Imagine for a moment, NetBackup is your guard dog. You want your dog to alert you if someone is peaking in your windows or testing your locks, but you don’t want to be alerted if it is a delivery driver bringing you something you ordered. Just like training your dog to know the difference between approved actions and questionable behavior, Veritas UBA will learn based on your actions to ensure you are receiving the right level of alerts for your system.
Unified SIEM Integration
Veritas Alta Data Protection and NetBackup allow you to monitor anomalous admin behavior within your Veritas environment. But sometimes, it’s useful to get the bigger picture. That’s why we partner with Securonix, who offer a Unified Defense SIEM Platform so you can monitor user activity to detect actions or patterns that could indicate malicious activity or compromised credentials. With the continuous monitoring of user activity, organizations can improve security, and when the time comes, ensure you have reliable cyber recovery. Learn more about enhancing data protection with Veritas and Securonix.
Veritas 360 Defense
Anomaly detection and malware scanning improvements are just some of the security enhancements in the latest release of Veritas Data Management Solutions. Learn more about our blueprint for defense in our solution overview.
