Hackers are in, now what?

The game has changed. I’m going to be bold and say it clearly, at this point everyone should operate under the assumption that hackers are already in your systems or could easily access them tomorrow. It’s very clear that savvy, sophisticated cybercriminals have been consistently getting past even the best front-line security for a while now. Their strategy is a smart one; lay low and remain hidden. Why? Their top priority is to observe and learn, all with the intent to find your weaknesses and exploit your vulnerabilities while waiting for the optimal time to strike. Of course, they will continue to get savvier and develop technologies to become harder to detect and/or avoid detection altogether. So now what?
Let’s take a quick step back. What are we talking about here? Well, it used to be that ransomware would get into a system, start encrypting, and download as much as it could, only to escape before it was detected. But ransomware has evolved. Ransomware criminals have taken a few plays from the organized crime playbook. They mimic the art of “casing the joint,” getting in and out when time is optimal to inflict maximum impact. They have perfected the art of cyber-reconnaissance. This practice, often called dormant ransomware or sleeper ransomware, is now a regular occurrence in the digital world.
Bad actors are highly motivated to cause as much destruction as possible to make more money and maximize their efforts—just as with any business, it’s all about ROI. Some reports suggest that ransomware sometimes lays dormant for up to 18 months. The bad actors know that optimal destruction depends on multiple factors like timing and scope. They want you to have zero choices BUT to pay their ransom. The old days of a breach and attack happening at the same time are long gone. This added complexity means that they can often know your systems better than you do, therefore the chances that they launch a series of events designed to disrupt and disable critical systems to net larger payouts are rising drastically.
So, what should you do today to combat this new dormant ransomware strategy? The good news is that some practices and technologies help you detect threats before the bad actors can take action. You can also use strategies to reduce the attack surface and prevent large-scale disruption and disablement once they are inside your environment. Here are the top six!
1. Illuminate with Infrastructure and Data Visibility
Attackers are looking for the weakest areas, those dark places where you may have limited security or oversight. Therefore, it is vital to implement tools that provide full infrastructure awareness, shining a light on all those dark areas, or dark data, in your environment. According to Veritas Vulnerability Lag Research, 35% of data is still dark. That is alarmingly high. We recommend you get to work on knowing what data you have and where it is ASAP.
Great best practice: In addition to full visibility of everything in your environment, it is also vital to have clear hard copy documentation on the details of your environment like procedures and configurations—including IP addresses, passwords, etc.—to help aid with recovery. Missing these details can keep you and your team from quickly recovering in the chaos of an attack. Store these in a safe that you check and update regularly.
Watch our demo video to gain insight into how Veritas provides full infrastructure and data awareness.
2. Protect All Data, From All Sources
Once you know where all your data and all your sources are, then you can safeguard them with multiple layers of protection to reduce attack surface and limit access. After sneaking into your environment, cybercriminals often search for confidential information or login credentials that will allow them to move laterally across your environment. They are highly motivated to gain access to your backup systems and attempt to eliminate recovery options. There are a few things that you can do to help mitigate this practice.
For starters, limit what and where each set of credentials can operate and have different passwords for every domain. Make sure that there is not one god-admin that can do everything. It is important to lock down or limit executive’s access as they are often easy targets, but just as important limit admin access and privileges, especially to backups.
Common practice is to adopt Zero Trust posture across your entire environment and implement MFA and RBAC.
Also important is to segment or microsegment your network into multiple zones of smaller networks and ensure access is managed and limited, especially to your most crucial data. Don’t let the bad actors get very far. Get creative with it. Meaning, be unique and set up a system unique to your needs and security requirements. When the Metropolitan Transportation Authority of New York, basically the New York subway, was hacked last April, hackers did not gain any access to systems that control train cars nor was any customer information compromised. Why? Because they have a multilayered, segmented network of over 18 different systems. Only three of which were compromised. This creative system prevented the threat actors from moving throughout the network; the event was isolated and restored quickly.
Great best practice: Create a walled-off network that looks exactly like your production network but with different management credentials. Share nothing with your production networks except access to immutable storage. You will use these spaces to recover your data and services, and scrub your data of malware. It is also a great place to test recovery.
Along the same lines, it is important to use an Air Gap Solutions (which we will break down in the next section.) One domain is no longer good enough. Keep vital infrastructure functions off the web. Store configurations of key services like backup, name services, network, and authentication services in a separate place.
Watch our demo video to learn how easy it is to set up RBAC on NetBackup.
3. Implement Immutable and Indelible Storage, and an Air Gap
A fantastic method to safeguard your data from being tampered with is to implement immutable and indelible storage, which ensures that data cannot be changed, encrypted, or deleted for a determined length of time or at all. Here is an excellent blog on our Multi-Tiered Immutable Architecture by my colleague, Roger Stein, and if you are looking for a deeper dive, a technical white paper titled Secure by Default, NetBackup Flex Scale.
At Veritas, we recommend the 3-2-1 backup strategy plus an extra 1! The 3-2-1+1 methodology is at least three copies of your data, at least two distinct medium types (like disk and cloud), at least one offsite or segregated copy of the data, and at least one on immutable storage.
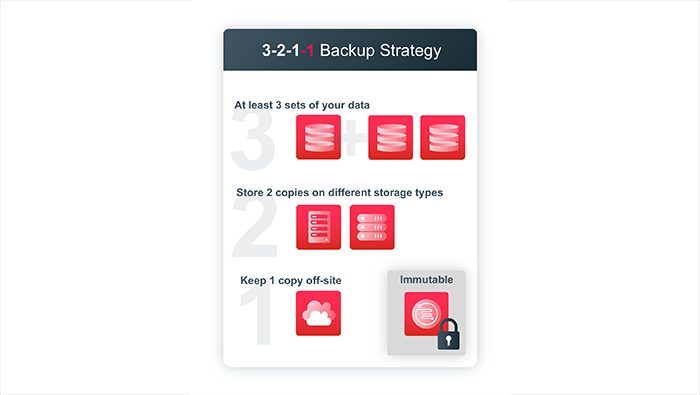
Veritas NetBackup can easily and automatically ensure no single point of failure by configuring lifecycle policies that send data over to a secondary or even tertiary domain. We call this technology Auto Image Replication or AIR. With AIR configured your data can be sent unidirectionally to a secure second location that can have different credentials configured and limited network capabilities ensuring proper segmentation of your data protection environment. It of course doesn’t stop there, utilizing the same automatic lifecycle we configured for AIR we can also send a copy of deduplicated immutably stored data to the cloud.
Another important security protocol is to create an Air Gap or a physical separation or isolation of devices, systems, networks, etc. to include, nothing but air. This can come in the traditional form of Tape, but it can also include hardware, software, and cloud air-gapped solutions. In addition to the traditional forms, Veritas offers a NetBackup Isolated Recovery Environment. Learn more about it here: http://vrt.as/nbu-ire
Great best practice: At first, make immutable storage your second copy, but once you get comfortable with your retention policies, make it your primary copy.
Watch our demo video to learn about how Immutable and Indelible WORM storage using the NetBackup platform prevents tampering with your data.
4. Adopt Anomalous Activity Detection and Malware Scanning
Next, implement tools that provide detection of abnormal behaviors or activities of both data and user activity. What do we mean by that? Put concrete and automated measures in place to alert if anything happens that is out of the ordinary in your entire environment. This could be things like unusual file write activity that could indicate an infiltration, but it could also be detecting known ransomware file extensions, file access patterns, traffic patterns, code downloads, access requests, storage capacity surges, external traffic paths or even an unusual jump in activity compared to individuals typical patterns. It is vital to be notified immediately of anything out of the ordinary. Here is a great example.
In the infamous SolarWinds hack, hackers used a regular software update to slip some elegant and innovative malicious code into a multitude of companies using the SolarWinds software. For over nine months, they roamed around some high-profile and sensitive companies, hiding in plain sight, learning their systems, gathering intelligence, until they made the mistake of roaming around the cyber security company, FireEye. The security team at FireEye noticed strange and suspicious activity, someone trying to register a second phone onto the company network. Finding it odd that an employee would have two phones, they jumped into action and called the user. Surprise, that user did not register that phone and had no idea who did! Thanks to the vigilance of FireEye, who conducted an investigation of out-of-the-ordinary activity and discovered the intrusion.
Great best practice: Conduct cyber threat hunts regularly. Take it seriously and implement tools to detect with protocols for investigating anomalous behaviors and malware.
Watch our demo video to learn about the powerful advantage of anomaly detection.
5. Optimize for Flexible, Rapid, Hybrid Recovery, At Scale
With “the bad actors are already in” mindset shift, resiliency and rapid recovery become the ultimate goal. We are talking about so much more than just a restore point, a single backup copy, or making multiple copies. You must architect an optimized and simplified recovery experience that will help you get back up and running, quickly, even at large scale.
To truly be optimized for the recovery experience it requires careful planning, orchestration, ability to have recovery options, cross-functional alignment and training, storage dedupe efficiencies and global visibility and oversight. With Veritas our solutions provide recovery from anywhere to anywhere and options that provide flexibility and choice in the event of an attack or disaster. Why is this important? Sometimes everything is impacted, and you may need to recover an entire data center in the cloud, on-demand. Maybe not all your environment is impacted, maybe just a portion, Granular File Recovery allows you to grab individual databases and files to very quickly recover back to production. In the case where entire servers become encrypted Bare Metal Recovery allows you to quickly recover that entire server elsewhere. Maybe you just need to recover a large amount of VMs back to production. We make that easy too!
Great best practice: Multiple disparate backup solutions by design create a complicated recovery experience—especially when multiple systems are compromised. Simplify and streamline by reducing the number and variety of point products and vendors across your organization.
Watch our demo video to learn how easy it is to recover with Veritas.
6. Orchestrate Non-disruptive Recovery Rehearsals
Cybercriminals hope that your organization is like most—not optimized for recovery. They want maximum damage and downtime to assure payment of ransoms. If you are ready and rehearsed for recovery, then you are a huge step ahead. To get to rapid recovery you must have a cybersecurity response plan for your entire environment, that includes testing early and often. Yes, regular rehearsals of your recovery help to limit downtime and disruptions and reduce the impact of an attack. Veritas makes it easy and efficient to execute non-disruptive tests with rehearsals that are automated and assured while leveraging non-production resources such as network fenced and sandbox environments.
Great best practice: Veritas also suggests that you rehearse recovering everything and not just a subset of your applications. Including things like your name service, authentication, system time and other infrastructure services as you will most likely be recovering most or all of your production environment.
Regular rehearsal and validation are vital for success because when you are in crisis mode, things need to just work.
You have the power to take important steps to combat ransomware and flip the tables on cybercriminals. By implementing a multi-layered ransomware resiliency strategy that includes these best practices and impeccable cybersecurity hygiene, you can stop attackers before they gain a foothold and give yourself some valuable peace of mind. You have heard it before and I will say it again, when it comes to a cyber security event or ransomware attack, it is no longer if, but when. Over the past year, we have witnessed a large number of examples of what not to do.
What’s the only thing worse than a Ransomware Attack? Mishandling one.
Veritas bolsters your cyber-resiliency with proactive protection of your data, AI-driven detection of threats, and industry-leading rapid recovery, at scale.
Click here to learn more about strengthening the resiliency of your organization.
Watch this informative demo video that shares how easy it is to rehearse recovery with Veritas.
