Hybrid and Multi-Cloud Data Security in Australia

Hybrid and multi-cloud management serves as a cornerstone of modern business operations. It stands at the forefront of leveraging cloud capabilities. However, this technological advancement comes with a critical need for robust security measures to protect sensitive information. Enterprises are navigating a maze of independent decisions made by various departments regarding data and storage. The capabilities and opportunities of the cloud and the inevitable data sprawl comes a larger need for data security to protect the business and minimize attack vectors.
Cloud Data Security
Australia has consistently been at the forefront of cloud computing. Enterprises have made significant strides in their cloud journey. The focus has now shifted from initial adoption to more sophisticated strategies like migrating critical applications to the cloud and multi-cloud environments. To effectively safeguard and manage risks, the Australian government has implemented a strategy to bolster cyber resilience and empower businesses to strengthen their defenses.
In Australia, hybrid and multi-cloud computing presents businesses and regulators with security risks. Protecting cloud stored data across multiple providers and several environments is crucial to prevent cyber threats, data breaches, and compliance issues. Organisations must focus on cybersecurity measures to safeguard sensitive information and ensure adherence to regulations.
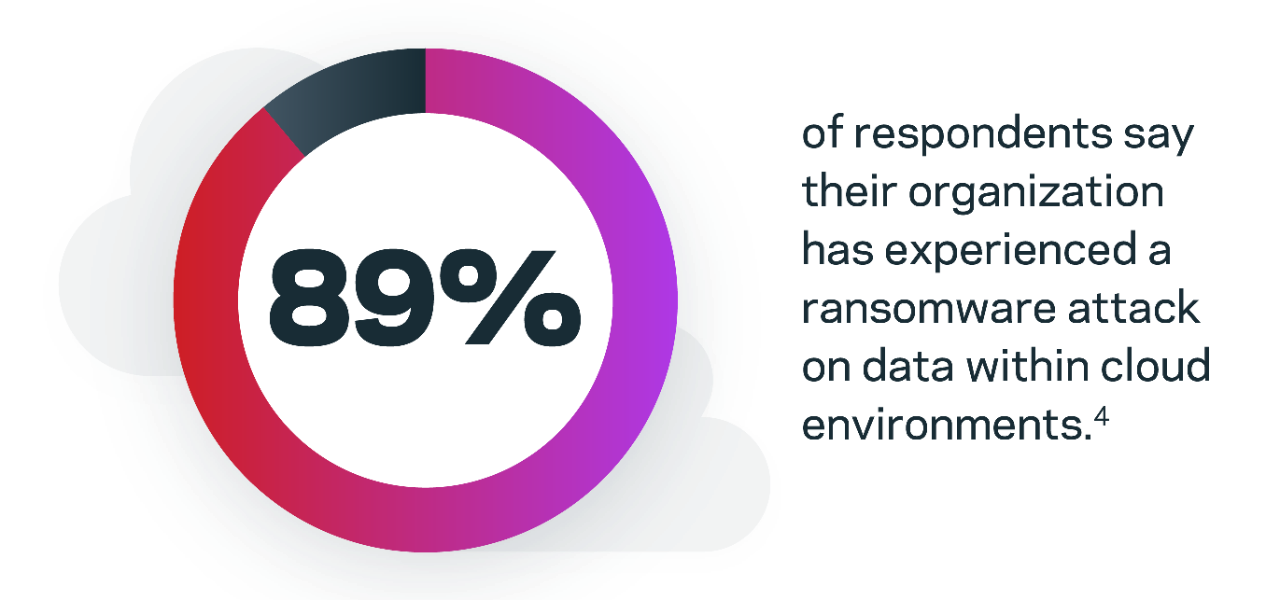
Click on the image to see the complete infographic
Key Considerations for Hybrid and Multi-Cloud Data Security
Strategy
In the future, no business will depend solely on a solitary cloud provider. Organisations are rethinking their plans for cloud computing based on factors like the high cost of data migration and increase in cyber threats. Adherence to data sovereignty and past investments to on-site data infrastructure are still a major roadblock of consideration.
To thrive in today's complex IT landscape, partnering with a cloud-agnostic provider, like Veritas, is crucial. These partnerships enable unified management solutions, seamlessly integrating enterprise clouds, networks, and data centers.
You Can't Do Everything By Yourself
Challenges extend beyond ensuring system security and resilience. It involves constructing optimal cloud architectures. You need to define management frameworks and identify which workloads should be in public or private clouds. Challenges also includes overseeing cloud migration and unifying workload and environment management through a singular interface. Many organisations lack the necessary in-house expertise to navigate these intricate tasks. Managed service providers play a pivotal role in closing this skills gap.
It is not enough to depend on a cloud service provider (CSP) to provide data security. To their credit, CSPs operating in Australia play a pivotal role in ensuring the security of cloud-based data. They invest in robust security measures to offer secure cloud environments for their clients. But the shared responsibility model highlights the need to have a robust security ecosystem to protect your data when a cyber incident occurs.
Prioritize Security and Compliance
The rising use of hybrid cloud environments create complicated risks. Ever-changing laws complicate compliance issues for organisations. IT infrastructures are diverse and difficult to maintain.
Global oversight concerning data privacy and cybersecurity require organisations to have comprehensive data security in place. Safeguarding customer data and ensuring adherence to the burgeoning array of laws and regulations is not a 'nice to have' but a 'need to have'.
To keep information safe, companies handling sensitive data must follow data privacy laws like the Privacy Act and the Notifiable Data Breaches scheme. These rules make sure that individuals' privacy rights stay safe and businesses need to keep data secure. In 2024 the Australian Government is set to introduce major reforms to Australia’s privacy laws. The goal is to strengthen security and data destruction obligations for businesses large and small.
At the core of the proposed changes, the government has agreed to overhaul how enterprises collect, use, and store data. These changes mandate organisations securely protect customer information that they store in the cloud.
Cloud platforms help organisations make compliance and security rules easier to follow. It can also allow for easier reporting. It's crucial for organisations to use specialized solutions that keep up with the latest rules and work well with their systems.
It is imperative to be able to identify potential breaches of personal identifiable information. It is also prudent to have the ability to delete records upon the conclusion of their mandatory retention period. Auditing capabilities prove invaluable when confronted by regulatory inquiries.
Things to Implement Now
Data Encryption and Access Control: Put in place robust data encryption protocols to safeguard data both in transit and at rest. Data encryption ensures that intercepted data remains unintelligible without proper authorization. Access controls limit the ability for cyber criminals or bad actors to move laterally across your environment.
Identity and Authentication: Adopt multi-factor authentication (MFA) and stringent identity verification protocols for an extra layer of security.
Cloud-based, air-gapped immutable storage for added security.
Regular Audits and Monitoring: Conduct regular security audits and continuous monitoring of cloud environments. This helps detect anomalies, potential vulnerabilities, or suspicious activities, allowing for prompt mitigation measures.
Challenges and Future Trends
Obstacles in securing cloud data persist due to evolving threats, the complexity of securing environments across multiple clouds, and a lack of skilled cybersecurity professionals. Advanced technologies like AI-powered security, Zero Trust architecture, and enhanced data encryption are changing Australia's cloud security future.
Securing data stored in the cloud is a continuous effort that requires cooperation among organisations, government agencies, and cloud service providers. To maintain data integrity, guard against cyber threats, and support trust in digital innovation, it is essential to maintain a strong security posture in the cloud.
As cloud technology advances, organisations must adopt a proactive security approach to shield its digital realm. Embracing this proactive stance is fundamental in ensuring the safety and integrity of Australia's digital landscape.