Detect Ransomware Early With Veritas Data Insight
Data Insight provides the analytics, tracking, and reporting necessary to deliver organizational accountability for file use and security. Designed to manage the needs of organizations with petabytes of data and billions of files, Data Insight integrates with archiving and security solutions to prevent data loss and ensure policy-based data retention.
When it comes to ransomware detection, Data Insight includes anomalous behavior detection, custom ransomware-specific query templates, and file extension identification that can all be used to detect ransomware.
Data Insight includes policy-based monitoring and alerting that is near real-time, which helps in detecting any malicious or anomalous behavior from user accounts.
It does this by scanning the unstructured data systems it monitors and collecting audits of all users read, write, create, delete and rename activities performed on the files as well as security and file counts for each user. It compares historical data it has collected and looks for statistical standard deviations to help detect anomalous behavior and identify accounts that might be compromised due to ransomware.
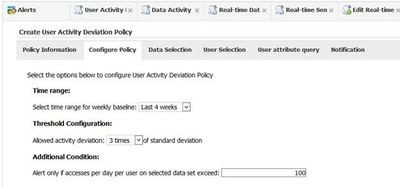
In addition, social network analysis, combined with anomaly detection, points out the malicious user accounts in the environment.

To provide more details on malicious or anomalous behavior and further detect ransomware specific activity, Data Insight includes various ransomware specific query templates.
These templates capture counts of activities such as writes and renames performed on the files by each user. If the count is higher than the specified threshold value, then the files on which the activities occurred could be exploited.
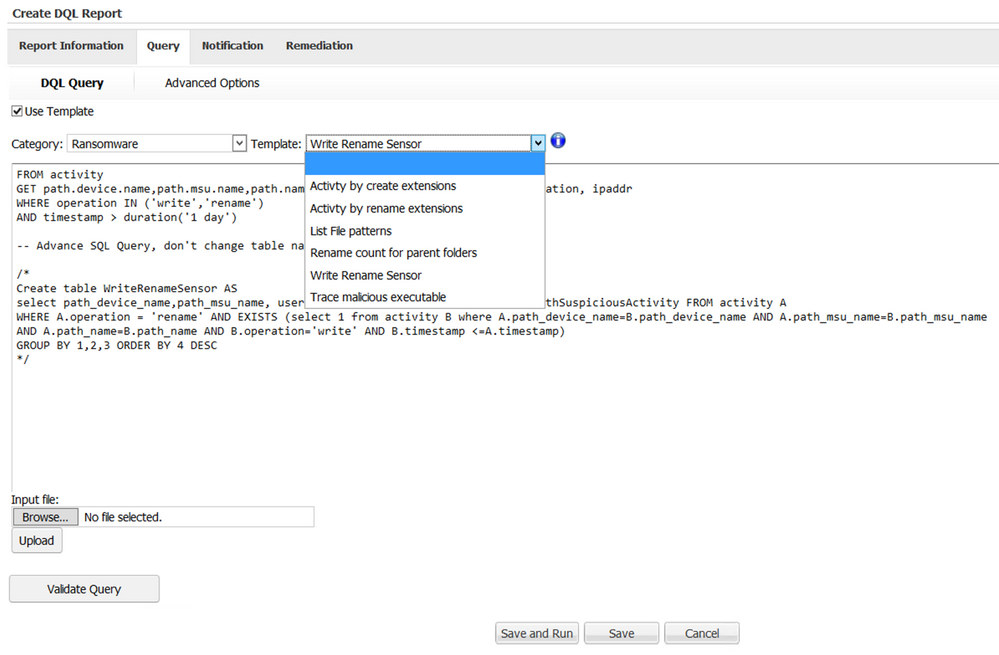
The following ransomware query templates are included with Data Insight:
- Write and rename query captures the count of write and rename activities performed by users on files within a data source within 24 hours. A SQL query is used to fetch the per-user activity (write) count performed on the file before it was renamed. If it detects any user who performed more than the configured threshold, the files on which the activities happened are termed as potentially exploited, and the appropriate users are alerted. By default, the threshold value is set to 100.
- Activity by rename extension fetches the count of files that are renamed per user and have unique file extensions. For example, the query extracts the number of files that are renamed, and which have the extension as doc, pdf, or xlsx.
- Rename count for parent folders fetches the top-level directories in the share, site collection, or equivalent, and the number of write and rename activities performed in each of these repositories per user. This helps detect malicious activities performed on the parent folder in a share or equivalent.
- Activity by create extensions lists all the files that are created in the last 24 hours per user. This is useful to identify files created by an infected or risky user.
- List file patterns lists the files that contain a specific string in the file name. For example, ransomware appends a unique extension to the encrypted files. With this query, you can fetch all the files that contain the specified extension.
- Trace malicious executable lists the duplicates of the ransomware executables residing on your system.
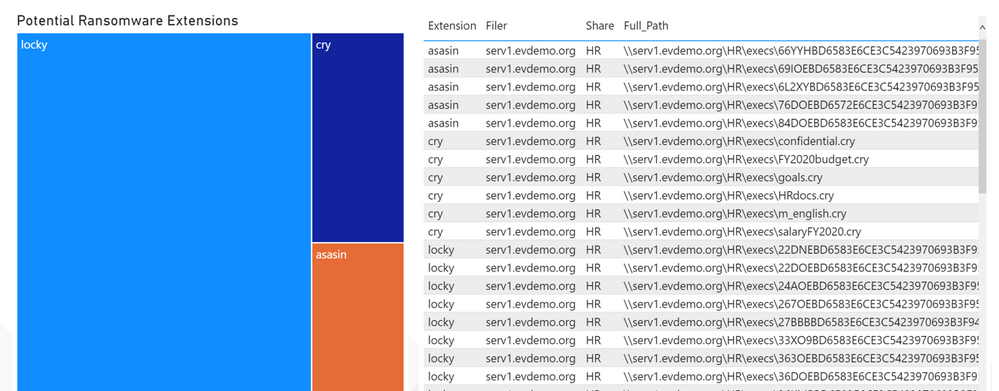
In addition, Data Insight captures file metadata, including file extensions. This information can be used to generate reports that can identify the location of known potential ransomware file extensions and accordingly take actions. This can be helpful to find ransomware infected systems and orchestrate remediation.
To read more about Data Insight, please see the Data Insight web site.
To read more about the ransomware report templates, see these sections: