Cybersecurity Hygiene—Top of Mind Following White House Memorandum

I have been wondering for a while now where the tipping point will be? What will be the final wake-up call that there is a cybersecurity crisis? When will governments get involved? Well, it is here; these questions are about to have an answer. This past week the US government declared that it would use similar protocols for ransomware attacks as it does for terrorist attacks. Why does this matter? This is fundamentally a massive shift in the approach and should help pull much-needed resources and international support toward this urgent and complex threat.
Ransomware attacks have been steadily growing and over the last year, hitting more and more essential industries like infrastructure, transportation, hospitals, police, and government agencies. Which has changed the urgency, bringing a greater sense of awareness and concern to how ransomware potentially impacts our day-to-day lives. We all feel the disruption when these essential industries are attacked, increasing the likelihood that companies will pay to alleviate it. Cybersecurity and cyberattacks overall are uncharted territory for governments. There are a multitude of questions, challenges, and approaches that will require formal laws and clarity. So, I see this progress from the US government as a crucial step in the right direction.
With the recent attack on the Colonial Pipeline, we saw a memorandum from the White House. But, frankly, not the enormous worldwide outcry I believe the event deserved. I recommend reading my colleague Alex Restrepo's article on the Colonial Pipeline for more details. This week we witnessed more shocking attacks: Fujifilm in Japan, which produces devices instrumental in processing COVID-19 tests, and JBS, the world's top meat producer. The White House addressed the JBS attack directly during a press conference on Tuesday, June 1. In a memo sent out on June 3, the National Security Council's top cyber official, Anne Neuberger, writes to corporate executives and business leaders that the private sector needs to better understand its critical role. "All organizations must recognize that no company is safe from being targeted by ransomware, regardless of size or location," Neuberger writes. "We urge you to take ransomware crime seriously and ensure your corporate cyber defense match the threat."
Alas, cybersecurity hygiene is the hot topic of the week. Rightfully so! It is a complex challenge that will require all hands on deck to combat; from employees and corporations, to governments and political unions. At Veritas, we urge you to take the threat seriously and prioritize an aggressive, multilayered cybersecurity strategy, cybersecurity hygiene, and always be prepared!
Here are some tips for impeccable cybersecurity hygiene to implement immediately:
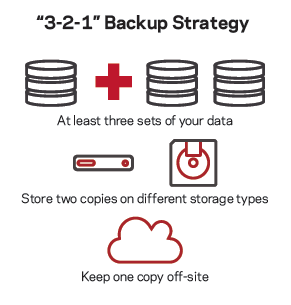
- Avoid single point of failure with 3-2-1.
- Update and upgrade all software regularly.
- Be prepared!
• Plan for an attack, put it in writing, and PRACTICE.
• Update your company's incident response plan and make it clear who is responsible for what actions in the event of an attack.
• Set up a communication channel on a secure texting app for senior leaders to communicate in the event of a cyberattack which may take down company email or chat systems. - Educate your employees; they are often the gateway to an attack.
- Be sure to enable multi-factor authentication on all company accounts, including service accounts and social media accounts, and that strong spam filters are in place. Never use factory passwords anywhere.
- Data Encryption at rest and in-transit.
- A modern AIR gap solution
- Keep the most vital infrastructure functions off the web.
- Implement data monitoring.
- Use immutable and indelible storage technology to prevent ransomware from encrypting or deleting backups. Read more in our Flex Appliances with NetBackup Security white paper.
- Review your company's cyber insurance policy and be sure that ransom is covered and that the level of coverage reflects the current reality.
- Assess the cybersecurity programs and protocols for your key vendors— particularly any entity that handles sensitive or critical company data.
- Hire a 3rd party agency to audit your team's strategy and check your work.
No company is safe. A multilayered cybersecurity plan along with impeccable cybersecurity hygiene is essential. We urge you to take the threat seriously. As Anne Neuberger writes in the official White House memo, "The private sector also has a critical responsibility to protect against these threats. All organizations must recognize that no company is safe from being targeted by ransomware, regardless of size or location."
Learn more about how Veritas can help here and read more about testing and other best practices in, The Path to Greater Resiliency: How to Recover from a Ransomware Attack.
