Automated Threat Hunting for Cyber Recovery and Cyber Security

Threat Hunting for Cyber Recovery and Cyber Security
Security teams leverage threat hunting for proactive detection of obscure and new cyber threats. Driven by threat intelligence, threat hunting provides a countermeasure to the continuous emergence of new malware and attack tactics.
Threat hunting also plays a critical role in incident response by providing insights on attacks that may have evaded traditional cyber security controls. In addition, threat hunting has emerged as a critical component in cyber recovery to aid the comprehensive decontamination of backup data. The decontamination dramatically lowers the risk of reinfection once organizations resume applications and services.
Threat Hunting is Resource Intensive
Traditionally, threat hunting relies on the process of conducting a thorough system wide search of threat indicators. This approach uses a wide range of technologies and techniques to analyze various data and logs before being able to reach a conclusion, making it time consuming. Additionally, processes that depend on continuous monitoring and data collection can become resource intensive. A balanced approach to threat hunting hygiene should also utilize tools that can be run automatically without being intrusive.
Hands Free Operation and Rapid Detection in Seconds vs. Hours
Malware hashes standardize and simplify the exchange of IoCs, or indicators of compromise, and with an updated list of malware hashes. Known malware hashes can be stored in a database and compared to hashes calculated for every file on a system. Since file hashes serve as a unique identifier, file hashes can be quickly retrieved and matched to known malware hashes without having to pry into contents of the file itself.
In the latest release, Veritas AltaTM is introducing a file hash search feature, complete with a file hash index. With this new feature, Veritas Alta will automatically determine if malware has proliferated across the backup data. First, all retained backup data is checked for indicators of compromise daily. Second, if a malware scanner identifies malware in a file system, that malware hash is automatically searched in other files systems, eliminating the need to do a full malware scan across the backup. Third, threat hunting can be used on demand to support forensics and investigations. A key outcome of this approach is that malware can be identified throughout the backup data using hash file index lookup with a 105 performance improvement over standard malware scanning*.
The file hash feature can be triggered in 3 ways:
- Automatically:
- Automated daily file hash search: Every 24 hours, a search is conducted using file hashes from customer uploaded hashes, 3rd party sourced hashes such as CISA, and malware hashes discovered by malware scan and is run on all backup images, consistently ensuring image health.
- Malware detected through malware scan: If malware is found in a malware scan, a hash value is calculated for that malware file. A hash scan is then automatically triggered using that known malware hash against all backup data.
- On-Demand: Customers can upload their own hashes and immediately search all backup data for matching file hashes, allowing security and backup teams to threat hunt as needed for forensics and investigations to support cyber recovery and security practices.
Veritas Alta File Hash Capability for Threat Hunting
The file hash feature has a few requirements to function properly, such as a database to maintain hashes for the file hash search. Additionally, file hash computation is required for each file when an asset is backed up for the first time and when a new file is discovered during subsequent backups. Because hash computation is a function of file size, the performance of the first backup where hash is enabled may be slow. However, hash computation only needs to be done when the file is first discovered or updated. Search operations are extremely fast as shown below.
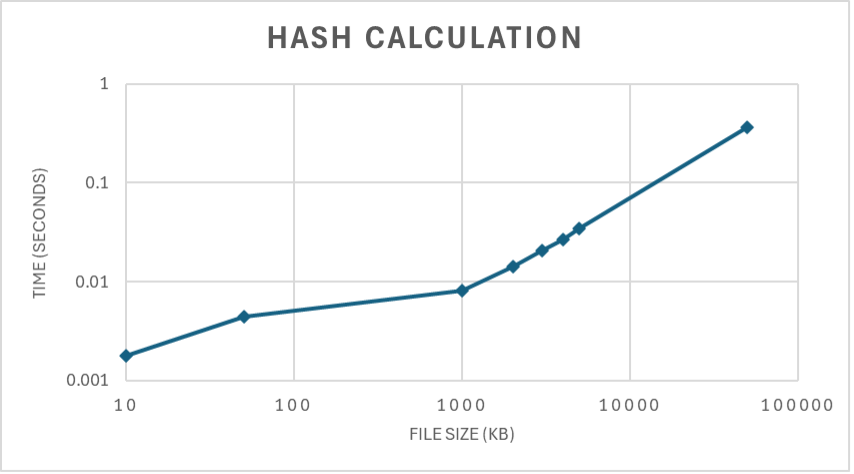
Figure 1: Hash calculation based on file size
The speed of the file hash scan accelerates threat hunting dramatically for cyber recovery, forensics and investigations. During a file hash search, if a match is identified, a notification will alert the user to the asset, backup, hash, and file paths. This kind of frequent and fast file checks can compress recovery time, allowing organizations to proactively recover their data before a malware attack. Malware scans that are scheduled with days between and need hydration can now be supplemented with a system that can identify malware quickly, compressing the react window from days to hours.
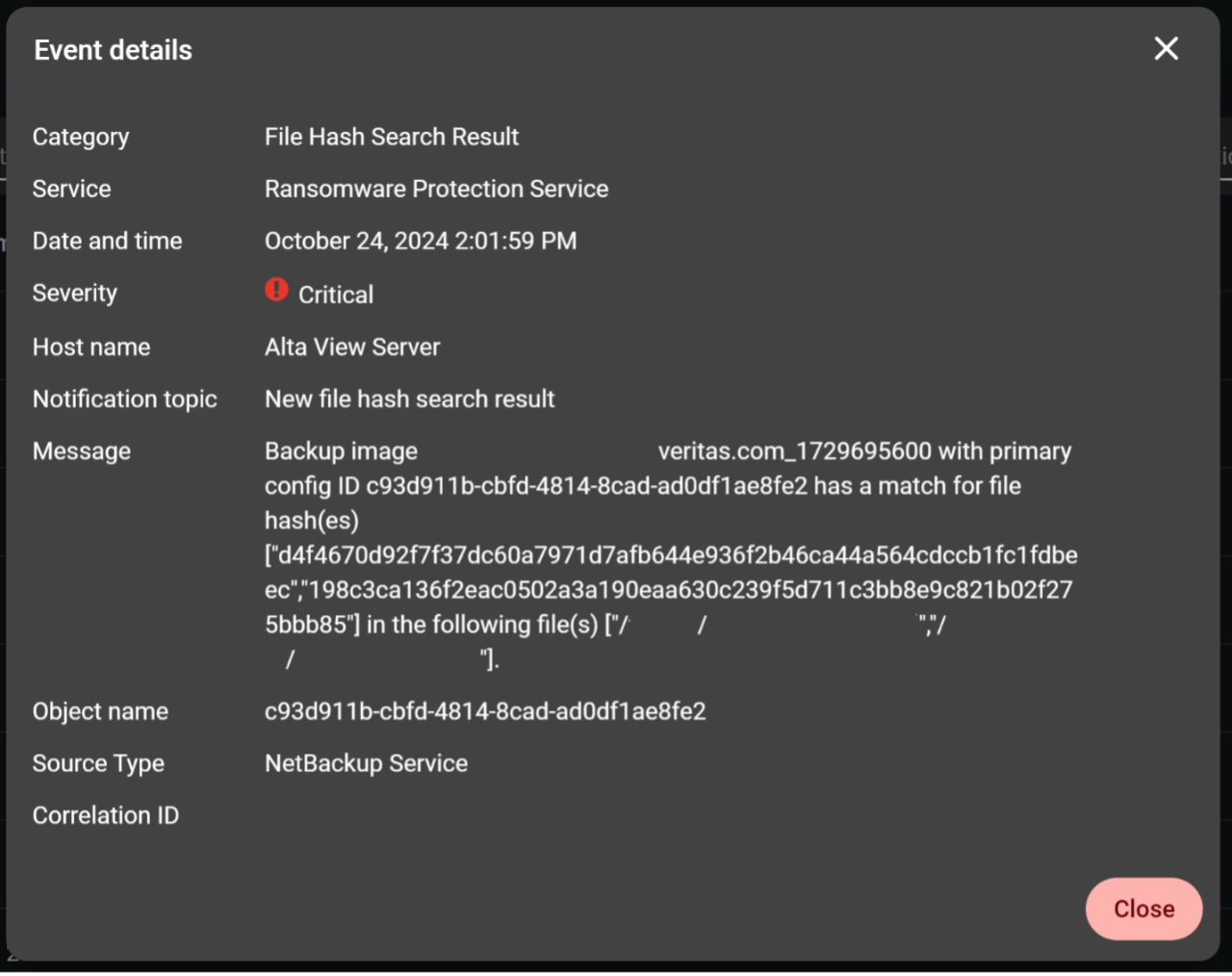
Figure 2: This is the notification to the user once the file hash search has detected a match. Within seconds of beginning the file hash search, users can know whether malware resides on their system.
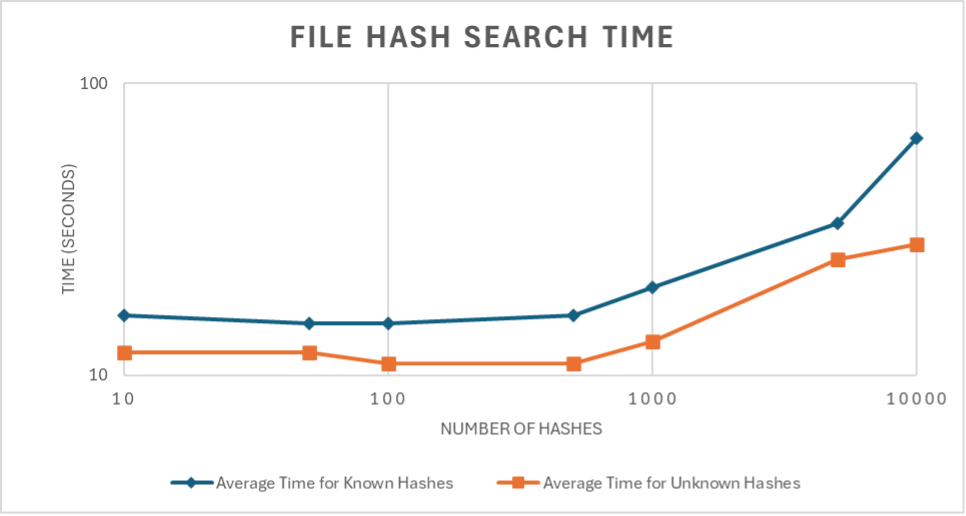
Figure 3: This is a representation of how much time it took for file hash search to run using a database with 10.7 billion file hashes with various number of hashes. This was done for both known and unknown hashes, with each file hash search time averaged over 5 iterations
Benefits of Accelerated and Automated Threat Hunting
For cyber security programs and for ensuring threat-free data for cyber recovery, threat hunting can be resource intensive for IT teams and infrastructure. With Veritas innovative threat hunting capability, threat hunting is accelerated and automated to deliver:
- Automated daily threat hunting across all critical data without disrupting production applications or services.
- Rapid and automated identification of malware proliferation within backup data when flagged by malware scanners.
- Accelerated data decontamination to significantly shorten recovery time following a cyber incident.
Key Takeaways
Cyber recovery teams need every advantage obtainable to identify threats and reduce cyber recovery time. By supplementing traditional malware scans with the Veritas hash index threat hunting capability, organizations will dramatically reduce the time to find IoCs in their backup data. With a 105 performance gain to identify IoCs, cyber recovery time will be significantly reduced as malware and IoCs can be instantly identified across files systems in the datacenter.
Learn more about Veritas Alta™ today or join the discussion on VOX.


