Cloud Storage and Data Encryption – How Businesses Can Protect Information in the Cloud

As companies adopt cloud storage, encryption is often a hot topic because the cloud means business data rests outside of the organization, on servers that the cloud provider can access.
Why Encryption is Important for Business
Corporate data contains sensitive customer information and valuable intellectual property. Mishandling information can result in fines, litigation, and brand damage. Encryption is one layer of security that can help protect company data from unnecessary exposure.
Deeper Motivations Behind Encryption in the Cloud
Your business may have compliance requirements or legal obligations to store data encrypted in the cloud.
For some, it is a checkbox feature. Being able to say “our data is stored encrypted” makes business leaders sleep better at night.
For others, there’s concern that the cloud provider may be used as a backdoor by the government to gain unfettered access to the company’s data. While this scenario does routinely occur with consumer / personal accounts in the cloud, it is rarely ever a tactic used against businesses.
Different Approaches to Encryption with Cloud Storage Using the Cloud Storage Provider’s Encryption
If you trust your cloud provider, then the easier method is to use their encryption at rest in the cloud. This means your data is not yet encrypted when you move or synchronize it to cloud storage. Your data should always be encrypted in transit, but in this case, the cloud storage provider receives it with access to the data. The cloud provider then stores the data and applies their encryption to secure it at rest.
This approach is ideal and suitable for most businesses. It is also the clearest solution because any user or application that is authorized to access the data can do so without worrying about a key to decrypt the data.
Relying on the cloud storage provider’s encryption-at-rest does mean the cloud storage provider could access your data since they maintain access to the keys. If your concern is the potential of your cloud storage provider acting as a backdoor into your data, then this approach to encryption does not solve your main concern.
Applying Your Own Encryption Before Sending Data to Cloud Storage
The alternative is to apply your encryption to the data you place in cloud storage. This requires that you manage the security of the key.
By encrypting your data before cloud storage, you are ensuring that only your business has access to it.
While the most secure approach, it does introduce some added complexities. As we have mentioned, you oversee key management. Also, running value-add features against your data in the cloud — things like analytics, content indexing for search, and self-service access for your user community — are blocked because these system processes or legitimate business users cannot easily access the data.
Pros and Cons of Cloud Storage Encryption Approaches
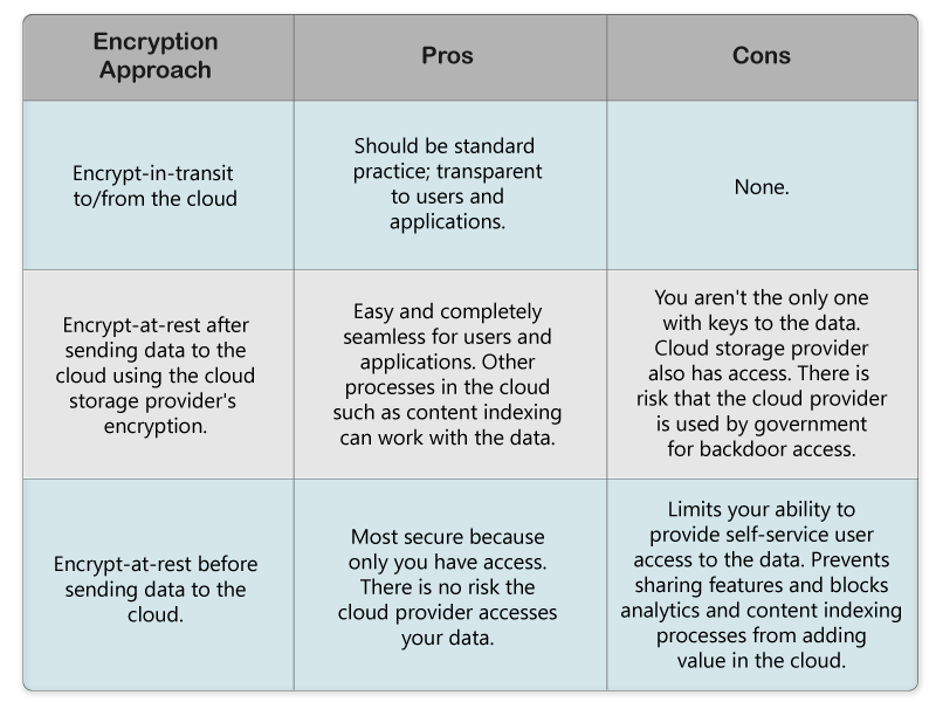
What approach to encryption meets your security and business needs?
Choosing the Right Approach
How you apply encryption to your data in your use of cloud storage depends on what you see as a risk. If your concern is the NSA gaining access without your knowledge or consent, then encrypting the data in your environment — with a key that only you have access to — before placing your information in the cloud is probably the approach you want to take. However, you also need to recognize the limitations and added complexity in handling your encryption. Most businesses today find it satisfactory to use the cloud storage provider’s encryption that is applied and managed seamlessly in the cloud.
How to Really Achieve Cloud Storage Security
People sometimes assume that encryption is the complete security solution for the cloud. However, encryption is just one layer of enterprise security. It is indeed an important component of cloud storage security, but there are other equally important facets of cloud security that must be present before storing corporate data in cloud storage.
At Veritas, we help companies solve their unstructured data challenges with cloud storage. This involves a full suite of security features beyond encryption to help reach the desired levels of enterprise security. For many organizations, the option to use the cloud is only possible if we can demonstrate that the security is stronger than what they have today. Veritas makes cloud storage more secure for storing and managing unstructured data workloads by adding security advantages such as:
1. Trusted Authentication, with optional Multi-Factor Authentication (MFA) and Single Sign-On (SSO)
2. Role-based Access Control (RBAC)
3. Access Control List (ACL) synchronization
4. Directory Synchronization
5. Data Leak Prevention (DLP)
6. Activity Auditing
7. Identification and Tagging of Personally Identifiable Information (PII)
8. No-shared-secret-ingestion to the cloud
Taking Your Unstructured Data Security to the Next Level
At Veritas, we are helping organizations archive their unstructured data in the cloud with the industry’s best security. If you would like to see how Veritas can make the cloud secure for your long-term data storage needs, connect with us today.
